The click cost $ 4M in Bitcoin in Visible Scams

Many of us have families to look after it. We save not only for our own future, but – maybe even more – for our children and grandmothers. We want to ensure good education, help them buy a home or just leave something for it when they need it.
Like Tony. He saved a significant amount for the future of his sons, more than $ 4 million in Bitcoin. And just one click, He lost everything to seeThe type of fraud that uses phone calls to cheat on people to give up sensitive information.
The scams are set as Google Support The agents and, after a complex scheme, first caught his attention, and then gained his trust and eventually left him nothing.
“Please, man. Is there anything you can do to return something to me?” She was tonya’s final, desperate pleading fraud, hoping to complain to their humanity.

The man who knocks on his computer keyboard (Kurt “Cibergui” Knutsson)
What does he see?
StimulateShort for “voice phishing” is a type of cybercrime that uses telephone calls to deceive individuals to discover personal or financial information. Unlike Traditionally stealingWhich relies on emails or text messages, an exam that supports the power of human voice and social engineering for manipulating victims. Commands often represent legitimate organizations, such as banks, technical companies or government agencies, to gain trust and create a sense of urgency. They may request passwords, credit card numbers or other sensitive details, which they use then false purposes.
Since the vision relies heavily on the tactics of social engineering engineers, it can be difficult to detect, making it a particularly dangerous form of cyber crime.

Hacker illustration at work (Kurt “Cibergui” Knutsson)
Best Antivirus for Mac, PC, IPhone and Androids – Cybergui Picks
Fraud is a good orchestrated game
Let’s split them up Vidher schemes to understand why they are so effective. Once you see them as an organized show that consists of different parts, becomes easier to recognize individual tactics.
ACT 1: Setup and targeting
Sectors begin by identifying potential victims through social media, public records on transactions, leaked databases and more. Once they choose a target, they collect personal data (email, phone number, financial resources) to build credibility. And it could easily be target. That is because Data brokers – Companies that buy and sell your personal information – are gold coins. Your whole profile is probably there, containing everything that needs to start successful fraud: Your name, address, contact information, family members, property owned and more.
How to protect yourself at this stage:
- Limit what you Share OnlineSpecial financial details
- Apply for Data removal services This deletes your personal data from the company databases
ACT 2: First Contact
The offsists always start contact first. Let’s walk through visual fraud using a Google account as an example.
- Starting the right security warning: Viewers can try to recover your Google account to quickly set safety alerts, such as verification codes to send you the phone. Their goal is not to reset the password, but to believe that there is a real issue of security.
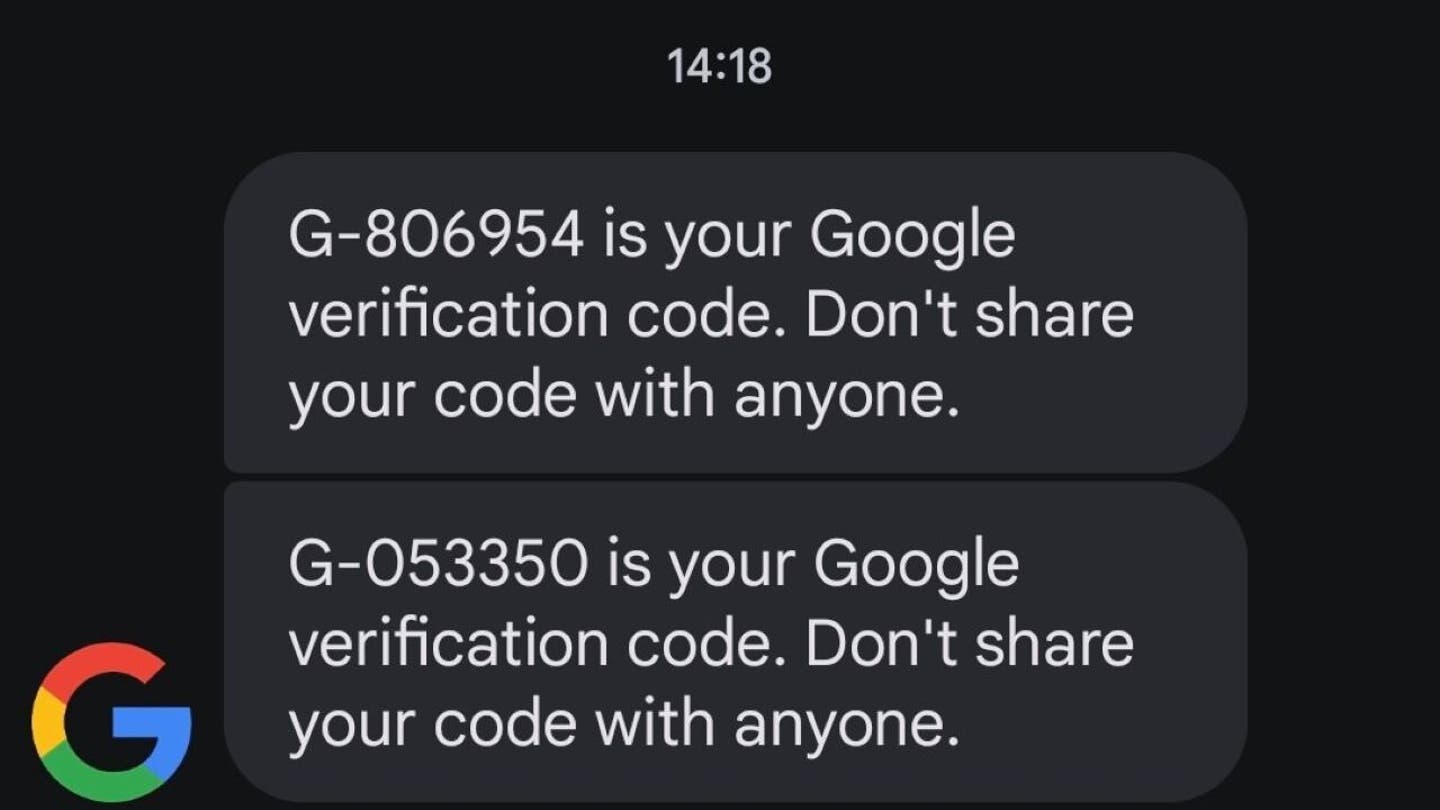
Google Verification Code Text (Kurt “Cibergui” Knutsson)
- Sending a false security message: They create a fake Google form using your email address, designed to mimic official security caution. The message often claims that there was a violation of security and to contact you soon an agent for appointed support.
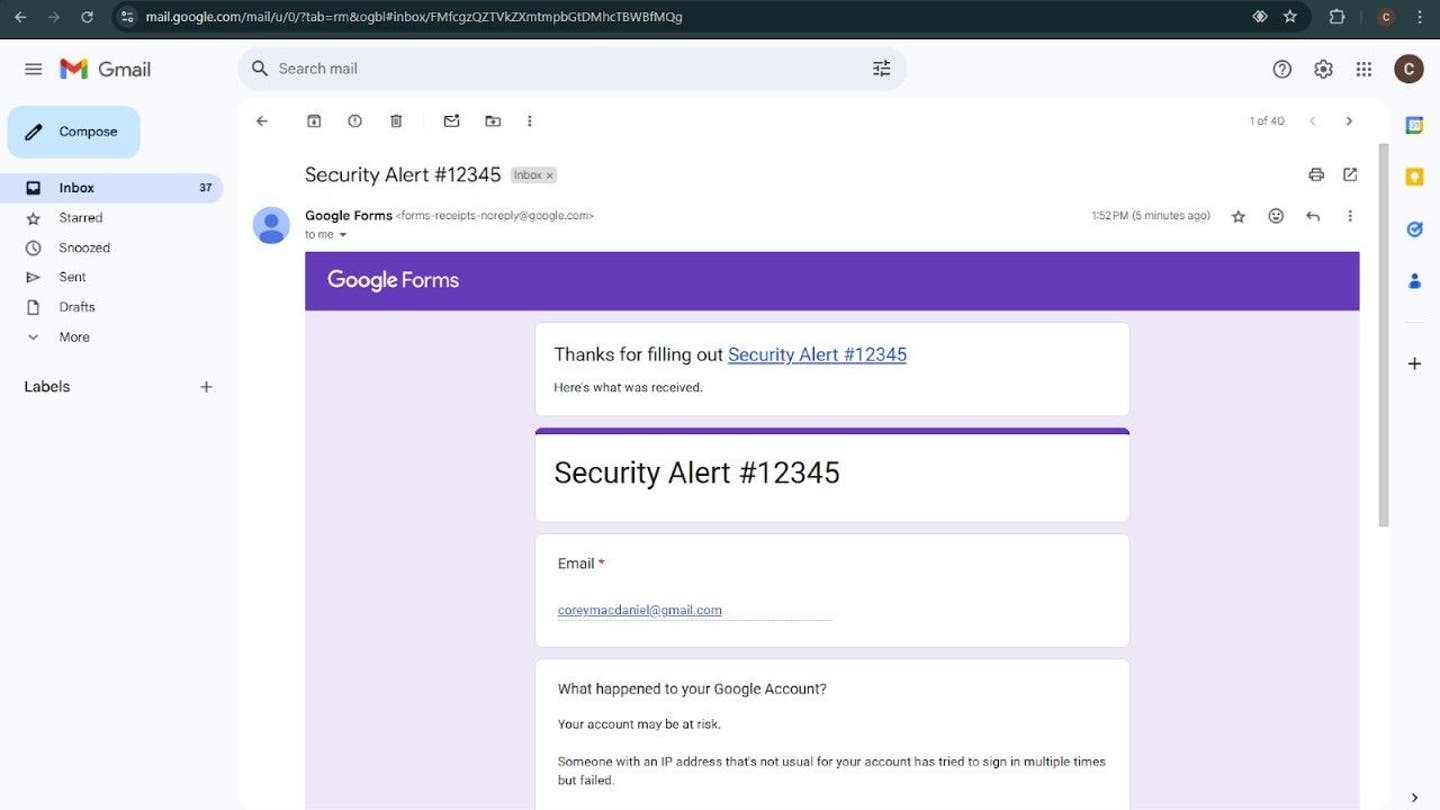
Fake Google Form (Kurt “Cibergui” Knutsson)
- Call setting: Shortly after you receive emails, the fraudsters call using the Spoofed Google number, taking you through fake security steps.
How to protect yourself at this stage:
- Pause and check – The rights of companies do not call you or e-respect for sensitive security actions
- Contact the company directly – Use official contact information (do not trust the number of callers or e-mail)
- Be skeptical at the emergency safety alerts – Scams create false emergencies to make you act without thinking
How to remove your private data from the Internet
ACT 3: Construction trust
Prepara no longer seek passwords. That trick doesn’t work anymore. Here’s what they do instead.
- We present yourself as funds to support: They remain calm and kind, claiming that they are there to help explore problems. They are referred to with a false Google shape that appear legitimate.
- Walking through the right password recovery process: While on the phone, fraudes make you change your password as a security measure. They do not send suspicious connections, but instead lead you through the right recovery process. At this point still don’t have access to your account. But that will change.
What is artificial intelligence (AI)?

Figure of the page for username and password (Kurt “Cibergui” Knutsson)
ACT 4: Fraud
After you successfully reset your password, fraudsters are looking for one last step: Sign up. There is a real fraud here.
- Sending a phishing connection: Now to trust them, send the message using the spoofed Google number with a sign-in connection. However, the connection leads to the website designed to look like Google’s login page.
- Logging in to the actual location: As soon as you enter your credentials in the fake page, the fraudsters are entered in the actual Google site. Seconds later, you get the original Google Security Feak to ask, “Is that you?”
- By clicking “Yes, that’s me” completes the scam: While you were on your false platform, they applied to your real account at the same time using your credentials. Google Security Row? That was not for your device. It was for theirs. As a result, you just gave cheats to access your account.
How to protect yourself at this stage:
- Never log in to your accounts Using the links sent to you
- Always Check the URL Before you enter confidential data and look for “https: //” and correct the spelling
- Use a Password manager that is automatically autofoiled in legitimate locations. High quality password manager ensures security with zero knowledge encryption, military class protection and support for multiple platforms, including Windows, MacOS, Linux, Android, iOS and main search engines. Search functions such as unlimited password storage, secure sharing, password health care, data misdemeanor, automatic copying and emergency access. See my professionally reviewed best password managers from 2025. Years
Hidden Free Application Costs: Your Personal Data
ACT 5: Head
At this stage, the scammers interrupt the call, leaving you feeling ease. You will not understand what happened until it’s too late. And these are not only Google Accounts at risk. The same method can be used to access Apple accounts, banking services and cryptocurrency wallets. For some, the loss of accessing Google is only pious; After all, Google Drive, Google Photos and other cloudy services store huge amounts of personal and financial data. But by the time you realize what happened, it’s too late.
How to protect yourself at this stage:
- Secure your accounts immediately – Reset passwords, enable authentication with two factors with an authentication application and log out of all active sessions to remove unauthorized access.
- Report and monitor for fraud – Introducing your bank, credit card provider or CRIPTO Exchange to freeze transactions if necessary. Report fraud on FTC (ReportFraud.ftc.gov), IC3 (IC3.GOV) and a plugged platform. Follow your accounts for a suspicious activity and consider credit freezing to prevent identity theft.
During the provision of your accounts and the fraud applications, it is crucial after the residence has already happened, the best defense prevents these attacks in the first place. Taking these steps can help you not to be a victim’s views of viring fraud first.
How to protect yourself from visible fraud
1. Invest in personal data removal services: These frauds all have one thing in common: they need some of your personal information to do. Without your name, telephone number or email, these fraud cannot happen. Codes can even try to get your trust by dividing more of your personal data, such as your social security number, look more likely. I strongly suggest you remove your personal information from the online search websites. If you give your email or phone number to someone, they may be able to find your home address through reverse search. Although no service promises to remove all your data from the Internet, having removal service is great if you want to keep track of and automated the process of removing data with hundreds of locations continuously for a long period of time. Check out my above selections for data removal services here.
2 Set the recovery contacts: Establish spare contacts for your accounts (Google, Apple and Bank) to ensure a way to access access if you lock yourself.
3. Monitor financial accounts: Check your financial accounts regularly for any suspicious activity or unauthorized transactions.
Get a Fox job on the go click here
4. Enable double authentication with two factors (2FA): Enable 2fa In all accounts, especially Google, Apple and Financial Services. This adds an additional layer of safety, which makes it difficult for trims to access your accounts even if you get your login details.
5. Safe devices: Ensure your devices are attached Screen lock or biometric authentication and hold Software updated to this day to prevent malware attacks.
6. Report fraud immediately: If you are cheated, report the fraud on FTC immediately on ReportFraud.ftc.gov and inform the affected platforms.
7. Use strong antivirus software: Install and regularly update strong antivirus software to protect your devices from malware, viruses and other cyber threats. Antivirus software provides real-time protection, scan malicious files and help prevent infections by blocking access to harmful websites and downloads. The best way to protect yourself from malware that install malware, potential access to your private information is that powerful antivirus software is installed on all your devices. This protection can also warn you of phishing emails and redemption fraud, keeping your personal data and digital funds. Get my choices for the best winners for protection from antivirus 2025 for your Windows, Mac, Android and IOS devices.
Kurt’s Key Water
Tony’s story is a cold reminder that even the earliest damage can become a victim of sophisticated fraud. These schemes visible, carefully orchestrated like a theater play, exploit our trust and exploit real safety warnings to gain access to our accounts. Protection We require constant consciousness, skepticism to unwanted communications and proactive measures for the protection of our personal data. Although the tactic can be developed, the basic principle remains the same: fraudsters rely on the deception for the exploitation of our vulnerabilities. By understanding their methods and taking prevention steps, we can force them to succeed.
Click here to get Fox News app
What more do you think companies and government should do to fight this growing threat? Let us know to write us on Cybergui.com / Contact.
For more of my technical advice and security warnings, subscribe to my free information newsletter in Cyberguy Cybergui.com / Novosletter.
Ask Kurt question or let us know what stories you want to cover.
Follow Kurt on his social channels:
Answers to the most favorable Cyberguy questions:
New from Kurta:
Copyright 2025 Cybergui.com. All rights reserved.
https://static.foxnews.com/foxnews.com/content/uploads/2025/03/2-one-click-cost-a-father-4-million-in-bitcoin-to-vishing-scammers.jpg
2025-03-05 18:00:00