Scheduled versions of the discovered video games are spreading
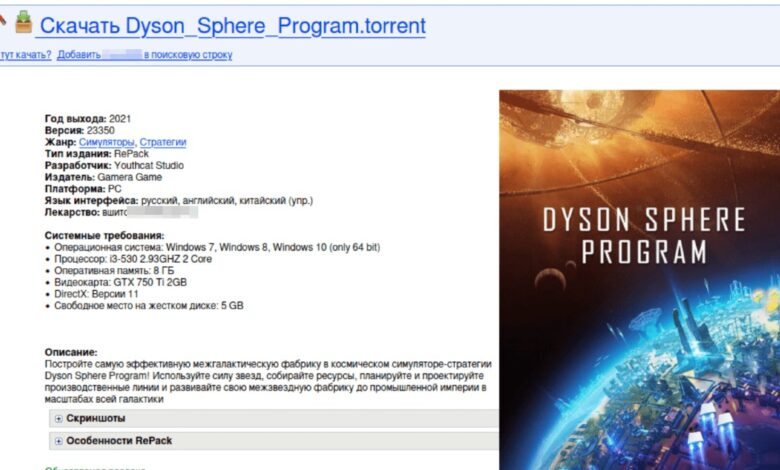
Scheduled versions of the discovered video games are spreading
Versions involved from games such as Gary modificationand Dyson sphereAnd The sand box of the universe They were employed in a global campaign for harmful programs.
A harmful electronic campaign launched on New Year’s Eve last year witnessed malware mining in the cryptocurrency installed on computers in Russia, Germany, Belarus, Kazakhstan and Brazil, according to a new report from the Russian anti -virus.
The malware campaign called Starydobry by Kaspersky Provessores continued for a month from December 31 and benefited from cracked versions of many famous video games, including Beamng.driveand Gary modificationand Dyson sphereand The sand box of the universeAnd plutocracy.
You are outside the free articles for this month
Games were distributed through torrent followers and shared by different authors, but they were all cracked in the same way, indicating a coordinated campaign.
While installing the actual game, the installer is first achieved to see if it works in the Sandbox errors correcting before checking the device’s IP address to determine its country. Then the device’s fingerprint is created, after which it installs MTX64.exe Malware Loader, which is presented as a system file.
The next step in the infection chain is to deceive resources to make harmful programs look legitimate. Finally, if the affected device contains eight CPU nuclei, the Miner XMRIG Crypto is downloaded and installed and installed. A mining server worker uses its infrastructure instead of being a public year and can close itself to avoid detection.
While the campaign victims were often private individuals, some organizations were also affected, but only because the employees have installed rift programs on business systems. Most of the victims were inside Russia, and the use of the Russian language in harmful programs indicates that it may also be the country of origin of the campaign.
However, it is difficult to determine the clear attribution to a well -known actor, according to Cassperski.
“Starydobry tends to be one campaign,” Kaspersky said.
“To deliver a mine transplant, actors have carried out an advanced implementation series that exploits users looking for free games. This approach helped the actors threatening to achieve maximum benefit from the transplantation of miners by targeting strong gaming machines capable of maintaining mining activity.”
David Holingworth
David Holingworth was writing about technology for more than 20 years, and worked in a group of printed nicknames and online in his career. He enjoys access to cybersecurity, especially when he allows him to talk about LEGO.
https://res.cloudinary.com/momentum-media-group-pty-ltd/image/upload/v1739928735/starydobry-campaign-spreads2_rpn9qm.jpg