Novi Crocodilus Malware Malware steals Android User User User Crypto Valler Keis


Newly detected Android Malware Dubbed Crocodilus Trikovče to users to provide a seed phrase for cryptocurrency wallet using a warning to make a key to a key to lose access.
Although the crocodilus is the new banking malware, contains fully developed opportunities to take control of the device, harvest data and remote control.
The researchers on the coverage previously devoured that the malicious software was distributed through the ownership drop, which detours Android 13 (and later) security.
Dropper installs malware without activation to protect the game, at the same time, bypassing accessibility services.
What Crocodilus Special makes it integrates social engineering that victims allow them to access their phrase seeds crypto-wallet.
It achieves it through a screen that warns the “Making a wallet key for a wallet in settings within 12 hours” or risk losing access to your wallet.
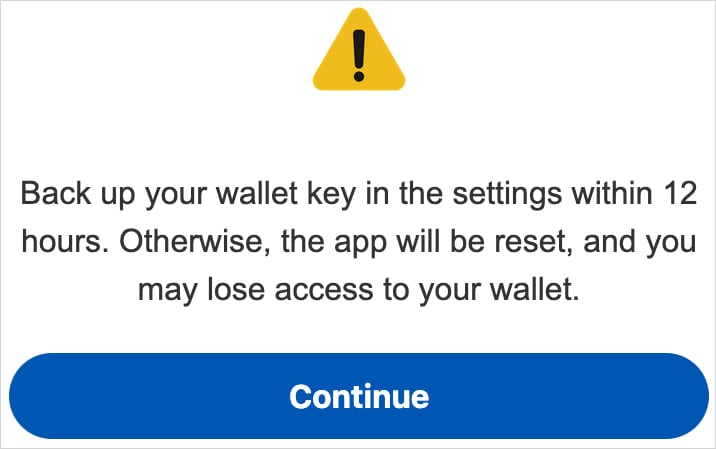
Source: Triploborne
“This social engineering trick leads the victim to move to their seed phrase, allowing the crocodile to beri text using his accessibility report,” threatful) explains.
“This information attackers can revoke full wallet control and completely empty it,” researchers say.
In its first operations, the crocodilus was observed targeted users in Turkey and Spain, including bank accounts from those two countries. Judging by messages to remove errors, the malicious software of Turkish origin seems to be.
It is unclear how the initial infection happens, but typical, the victims are deceived in the pickup droplets Through malicious locations, false promotions on social media or SMS and third-party applications.
When launched, Crocodilus gets access to accessibility services, usually reserved for helping people with disabilities, to unlock access to the screen content, perform navigation gestures, and launch monitor.
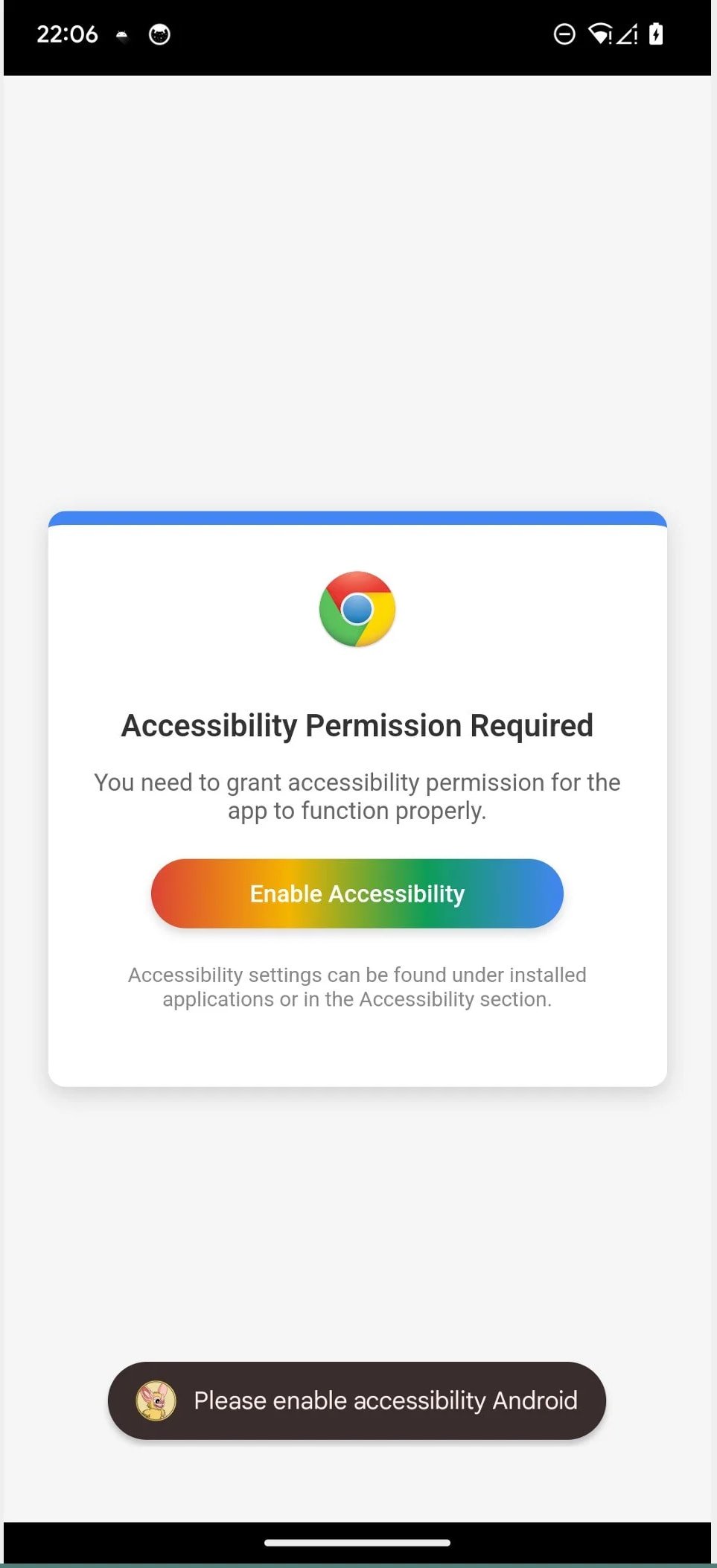
Source: Triploborne
When the victim opens a targeted banking application or cryptocurrency, crocodilus burdens a false cover on top of the right application to intercept the victim’s credentials.
The bot malware component supports a set of 23 commands that can be performed on the device, including:
- Enable call forwarding
- Start a specific application
- Send the key
- SEND SMS to all contacts or a specified number
- Get SMS messages
- Request the Privileges of the Admin
- Enable Black Cover
- Enable / Disable Sound
- Lock screen
- Make yourself the default SMS manager
Malware also offers the function of remote access to Trojan (rat), which allows its operators to touch the screen, moving in the user interface, run the gestures and more.
There is also a dedicated ratio command to record the Google Authenticator application screen and recorded a one-time password code used to protect two authentication factors.
During these actions, crocodile operators can activate the black cover on the screen and turn off the device to hide the activity from the victim and make it appear as if the device is locked.
Although Crocodilus seems to have specific targeting limited to Spain and Turkey, Malware could soon expand operations, adding multiple applications to its target list.
Android users are advised to avoid downloading APKA from outside Google Play and ensure that salary protection is always active on their devices.
https://www.bleepstatic.com/content/hl-images/2025/03/28/crocodile.jpg
2025-03-30 17:17:00





