Freedrain phishing fraud takes wallets with crypt cryste

Sophisticated phishing scheme, which contains a network of fake sites, targets Web3 projects and wallet drainage for cryptocurrency on a scale.
First, he discovered Validin as a simple network of crypto phishing sites in April 2024, it soon became obvious that the scheme could be much more sophisticated and large scale. This stated that the provider of the Internet Intelligarovance platform cooperated with the Sentinelone Research Team, Sentinellabs, in order to implement further investigation.
Instead of relying on common delivery methods such as phishing emails, SMS (deviling) messages, schema, called Freedrain by investigators, used SEO manipulation, free techniques for processing and layers of cryptocurrency.
Operation, which probably conducted a team based in India (or possibly Sri Lanka), is at least 2022. Years.
Wallidine and Sentinellabs published its findings on Pivotcon 2025, a conference on threats in Malagija from 7. to 9. May.
Detection of a large crypto-cyprus network
In April 2024. year, he confirmed the certificate of reports documenting a number of encryption pages for exhausting crypto-expression.
This report attracted the individual who contacted Valinov confirmed, claiming that 8 Bitcoin was lost at the time.
“The victim did not submit a clause for a wallet’s seed for Phishing, while trying to check his wallet balance, after clicking on a highly ranked search engine result,” Sentinellabs and Valine researchers explained Joint report 8. May.
The seed phrase, also known as a recovery or mnemonic seed phrase, is a list of words used to restore a cryptocurrency wallet and access associated funds.
It is confirmed by reliable analysts to monitor cryptocurlens that the destination wallet receiving the victim’s funds was a one-time address.
They stated that the stolen property quickly moved through the cryptocurrency mixer, the process of facility that fragments and means of funds in multiple transactions in multiple transactions make attribution and recovery almost impossible.
The researchers reported that although they were unable to help recover lost property, the exceeding effort revealed that the attack on phishing was part of wider, great work.
SEO manipulation techniques
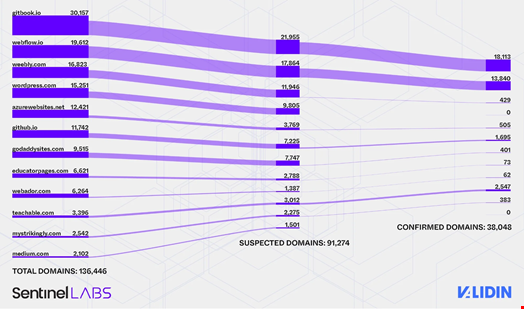
After further investigation, Sentinellabs and valid researchers identified 38,048 different painting directions. These subdomains are hosted on cloudy infrastructure, such as Amazon S3 and Microsoft Azure Web Apps, which mimically legitimate number of Cryptocurrency wallet interfaces.
In order for the networks to make lightweight to victims, hackers used the combination of SEO manipulation, free services, Github.IO, GitBook), basic visual elements and layers of redirection technology in a false sense of legitimacy.
“They set us on fire pure paqua volume that appear among the top search results all over all major search engines,” Researchers said.
“In most cases, the site consisted of just a recording of a legitimate crypto wallet interface), followed by several lines of text that offered seemingly useful instructions, ironically, and they were sought to form users how to form.”
While seemingly basic, these websites showed direct answers to questions, the search engine users will probably enroll. It is known that these types of pages reward search engines algorithms, especially when they host on platforms with high reputation.
In addition, freeDrain operators employed a large comment spamsing to poorly maintained sites to increase the visibility of their youth pages via search engine index – technique known as spam.
“This technique provides free traditional vectors for traditional deliveries such as phishing emails or malicious ads, instead of getting to know the victims exactly where they look, at the top of trusted search engines,” researchers wrote.
AI-AIDID CONTENT GENERATION
The text on many young sites showed evidence that they were generated by large language models, in accordance with investigators.
They stated that the copy artifacts found, revealing specific tools used, including wires like “4O mini”, probably reference to Openai GPT-4O mini model.
Investigators noticed that these signs suggested that freedom operators use generative AI to create scalable content, but sometimes they worked carefree.
Chain Attacks: Mood Step by Step
Sentinellabs and Valine researchers were able to outline step-by-step process that eventually leads to Phishing:
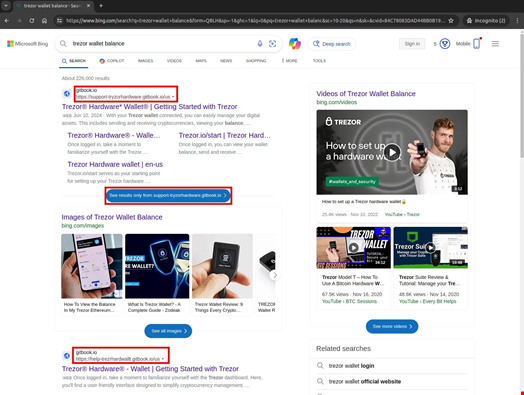
- Look for the inquiries related to the wallet (eg “VALLET BALANT”) in the large browser
- Click a high score, which was often hosted on a seemingly trusted platform like a gitbook.io or webflow.io
- Land on a page that displays a large image, which can be used (usually a Static Screen of the Legitimate Wallet Interface)
- Click on the image, which or leads to a phishing page or redirects the user to the intermediary site
- Come to the final backorder, almost the perfect clone of the right wallet, which requested the user to enter its seed phrase
Once a seed phrase is submitted, an automated attacker infrastructure will take funds within minutes.
Attribution of a campaign for freedom
Finally, investigators stated that it attributes a freedrain surgery challenging due to its ephemeral infrastructure and use of common, free services.
However, by analyzing the repository metadata, behavioral signals and time artifacts, managed to collect significant insights into operator characteristics, including their likely location, work processing and level coordination.
Researchers reported that their investigation revealed several key findings. They analyzed Github repository related to Freedrain and found that the email addresses used in the Commission are unique and related to individual github accounts, with most that came with free e-mail providers.
Moreover, the time regulations were predominantly predominantly in UTC + 05: 30 Timesone, which corresponds to Indian standard time (IST), suggesting a strong geographical connection to India – or possibly Sri Lanka.
This finding was confirmed by the analysis of metadata from other services, such as Webflow, which has revealed a clear form of working work work work of 9 to 5 weeks in the East Weather Zone.
The researchers concluded that, based on combined evidence, it was very likely that the freedom surgery was performed by individuals based in India, working standard hours.
They also noticed that the campaign was active of at least 2022, with a significant increase in activity in mid 2024. years and remained active at the time of their report.
Mitigation recommendations
Investigators recommend that the platforms contain free content take steps to prevent abuse and improve their response to maledrain, as Freedrain’s campaign (s).
- Improve mechanisms for reporting abuse by enabling abuse to apply directly from published contents pages and establishing direct communication lines with reliable threats Intel analysts and threat researchers and threat researchers
- Insert in basic preventive abuse tools for monitoring abuse forms, such as creating bulk orders, similar domain structures and repeat hosting sets for external phishing
- Improve detection options for identifying coordinated abuse, such as repeating forms of appointment and identical templates re-used by subdomains
https://assets.infosecurity-magazine.com/webpage/og/618a9981-320f-4741-af92-ceab8c822bf1.jpg
2025-05-12 15:30:00




