Feature of the remote control for misuse for abuse for crypto-stealing attacks


Hand Group called “elusive comet” targeted users of cryptocurrency in social engineering attacks that exploit the zoom remote control function for users to approve them access to their machines.
The zoom remote control function allows participants to meet with which to take control of the computer of another participant.
According to Cyber-Cyber-testers the trail of bits, who encountered this social engineering campaign, perpetrators of a mirror technique used by a group of hacking Lazar in Massive $ 1.5 billion cubit crypto Heist.
“Eluzian comet methodology is reflected in the technique behind more than $ 1.5 billion in February, where the attackers manipulated legitimate operating flows, not the exploitation of coding vulnerabilities,” explains the trail of the Bit report.
An interview scheme based on zoom
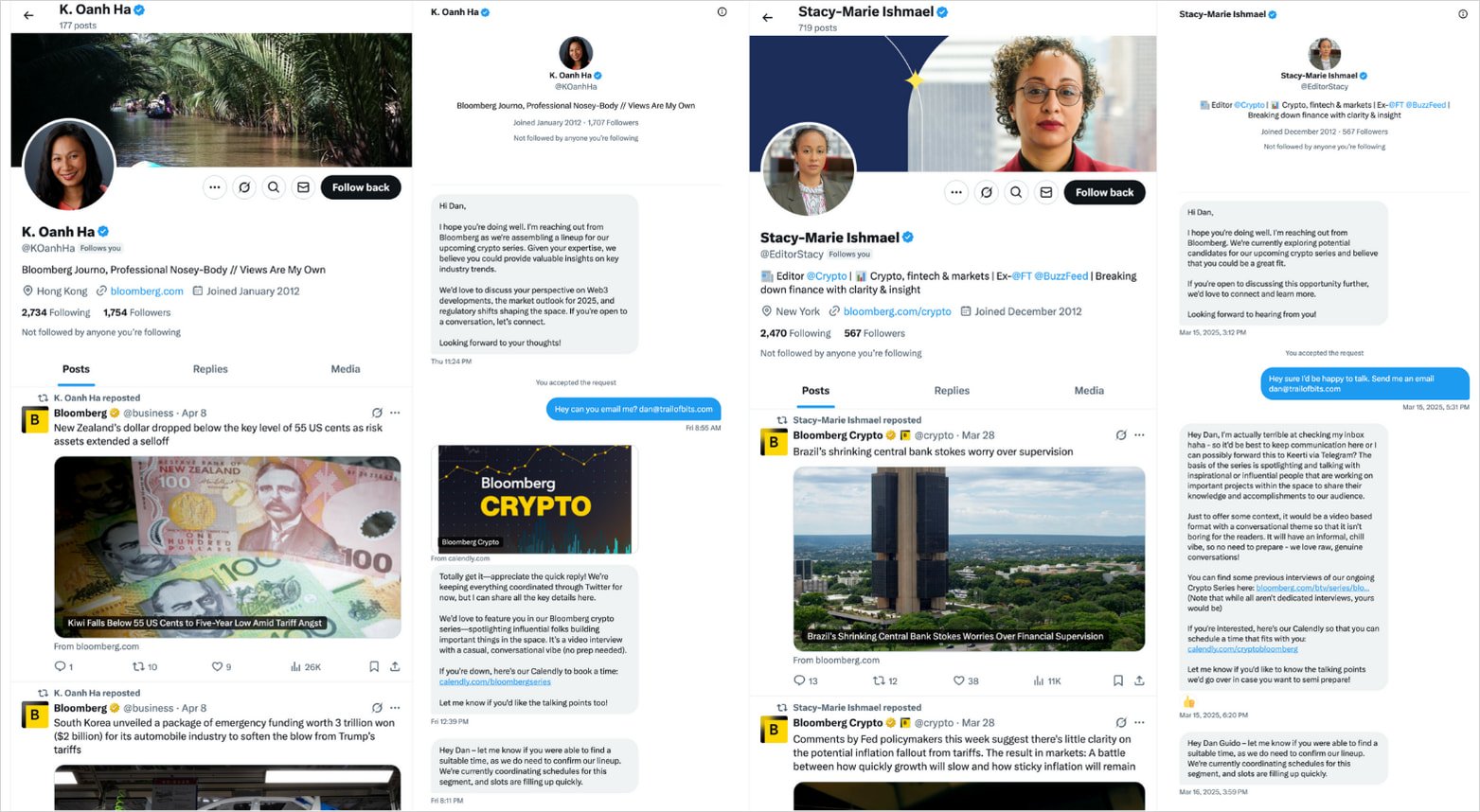
The Bita Track learned about this new campaign after the actors of threats tried to conduct a social engineering attack on its general director via X direct messages.
The attack begins with a call for “Bloomberg Crypto” interview via zoom, sent to high value goals via stamps with brands on X, or via email (BloombergConferences).
False invoices represent journalists focused on crypts or Bloomberg and reaching the goals of direct messages on social networking platforms.
Source: Track Bita
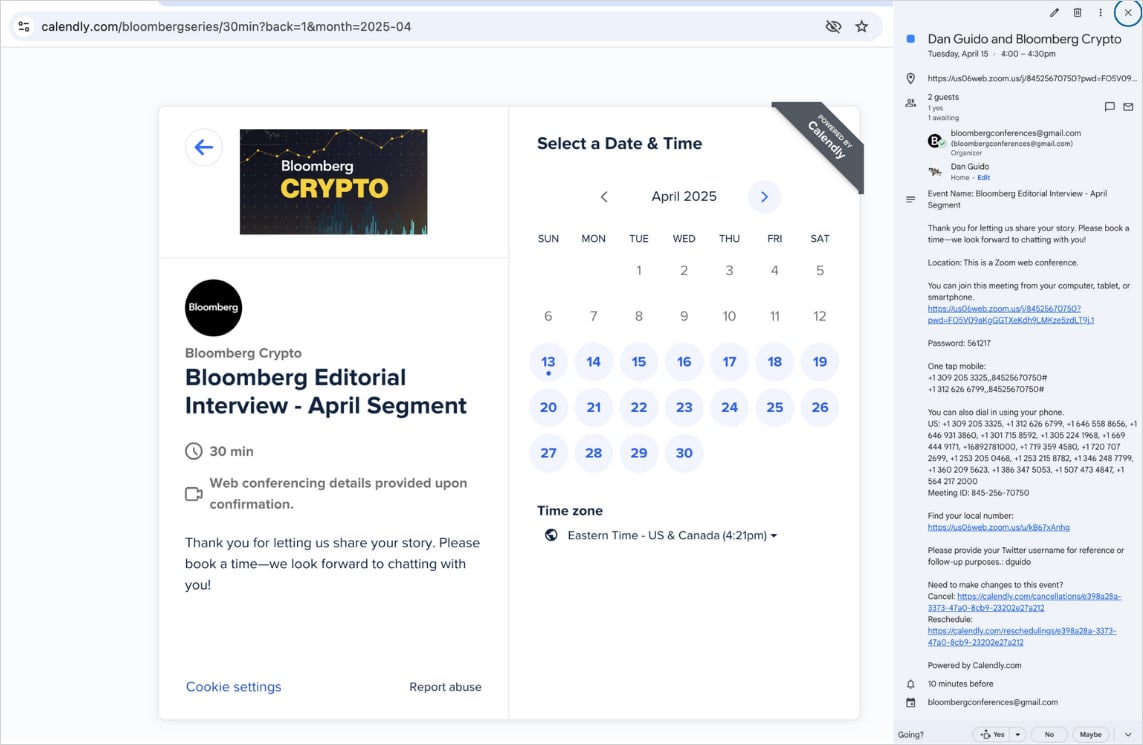
Invitations are sent to canteen links to schedule a zoom meeting. Since they are also in cancing and zoomed in invitations, they are working as they expect and reduce the doubts of the goal.
Source: Track Bita
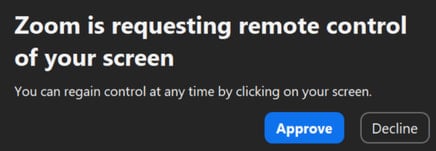
During Zoom call, the attacker initiates the screen sharing session and sends the remote control request to the target.
The trick is employed at this stage is that attackers rename their “zoom” zoom, so it is a quick sacrifice to read the “zoom requires the remote control of your screen”, which seems like a legitimate application request “.
Source: Track Bita
However, approving the requirements gives attackers to the victim’s full remote entry, allowing them to steal sensitive data, install malware, access files, or launches crypto transactions.
The attacker can quickly act to establish persistent access to the implanted backdo for later exploitation and shutdown, leaving victims with a little chance to realize compromise.
“What makes this attack particularly dangerous is the similarity of the license dialogue and to other indispensions of zooms” Says the trail of bits.
“Users located on the click on” Approval “on the zoom calls can approve full computer control without realization of implications.”
To defend against this threat, a trace of bits suggests that the application of system policy preferences (PPPC) that prevent accessibility approach, which is possible to use this Tool collection.
The firm recommends removing zoom completely from all systems for the security critical environment and organizations that manage valuable digital means.
“For organizations that deal with specially sensitive data or cryptocurious transactions, the risk of removing the zoom client fully exceeds the more inconvenience of using the search alternatives,” explains the trail of the bits.
https://www.bleepstatic.com/content/hl-images/2022/09/15/Zoom.jpg
2025-04-22 22:43:00



