Almost half of the stolen cryptors remain unspent, the data is displayed

Approximately 46% of hacking funds are seated in an empty time, suggesting opportunities to recover post-incident, analysts in the global book.
Hackers are fast, but the systems are chasing them continued. New report Global Ledger’s intelligence blocks, based on hundreds on chain incidents, shows that in many cases, stolen funds are landed on washing destinations before hacks are still publicly released.
On average, 43.83 hours are required from initial chain violation until the incident is notified on the victim’s project or third party investigator, according to the report shared with crypto.news. Meanwhile, hackers tend to cross stolen funds in the first identified entity, such as stock exchange, crypto mixer or decentralized finance protocol, within 46.74 hours.
The longest delay, however, the window between publication of public publication and interaction of attacks with washing service, which average 78.55 hours, which suggests that funds are often already known in motion.
‘There is no clear playbook here’
In total, the researchers of the global book measured four key deadlines in hundreds of incidents. The time of violations for the financing of movement, from misdemeanor to reporting, from the misdemeanor to the first entity interaction, and from the public announcement of the washing washing activities. Every Lag also tells his story.
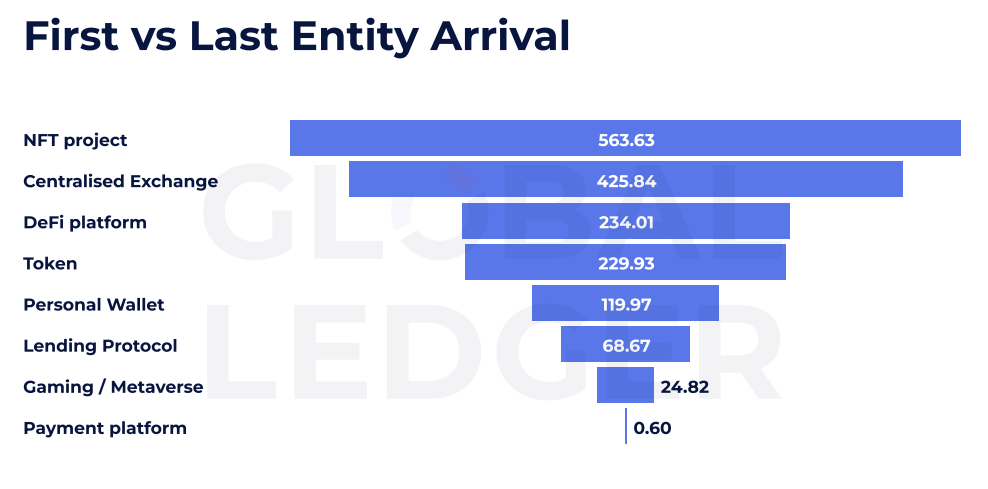
Attacks targeting Nft Projects, for example, show the movements of the slowest fund. On average, 563.63 hours – or almost 24 days – for funds from these feats to transfer from the first to the last known entity in the washing chain. It is more than doubled average lag seen in centralized stock exchanges, which hour in about 425 hours.
Global Books The Corporal and Director of Fisun said Cripto.News in the exclusive comment that there was a long delay – in the case of NFTS – it is not only low liquidity because these tokens are “unique and harder”. “
“There is no clear playbook here, washing usually involves trading or social engineering. Idole exploits idols, where the attacker earned $ 340,000 in Stema, but stuck with an associated NFTS.
Lexun
The report points out that wash roads vary depending on the type of projects exploia. DEFT platforms and tokens usually see the funds crossing the washing channels within 230 hours, while payment platforms show the fastest reversal: only 0.6 hours on average. Playing and Metavers They are exempted among faster flows, moving in less than 25 hours.
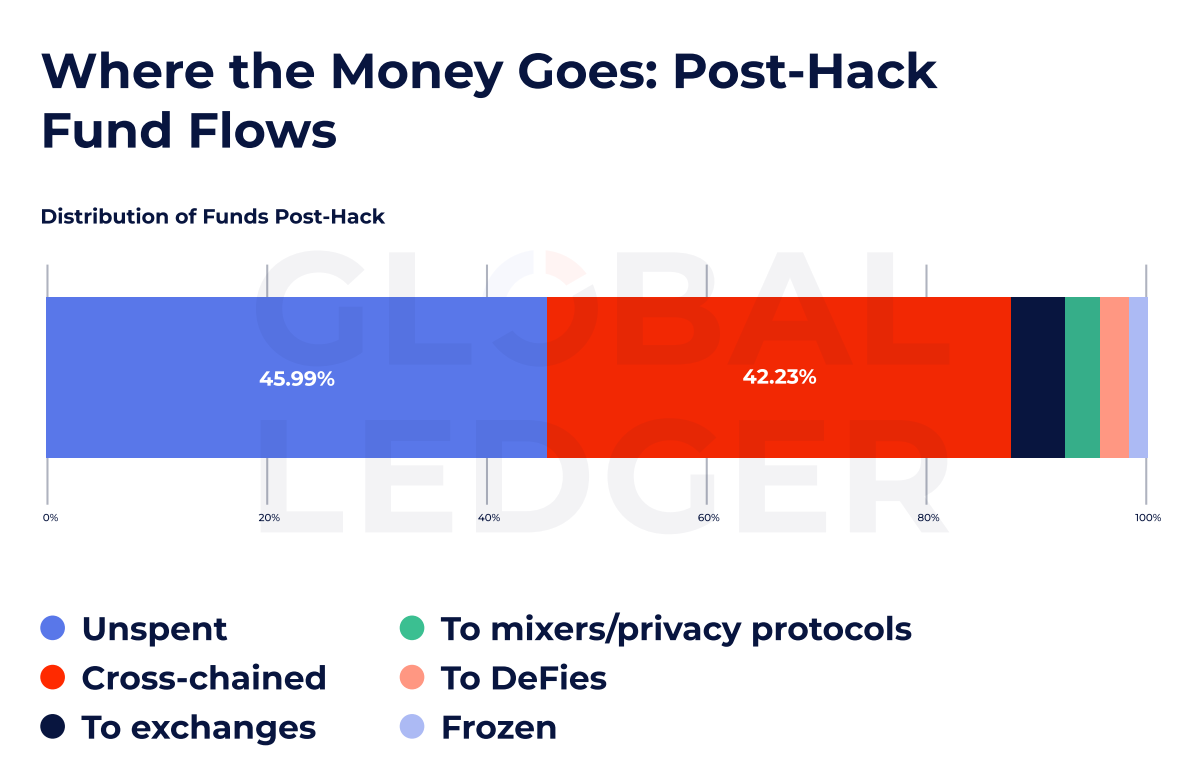
Despite the speed and fragmentation of the fund flows, the surprising amount of huck property remains intact. According to data, almost 46% of stolen funds remained unshaded, suggested significant opportunities for current monitoring and potential recovery, long after the incident occurs.
Cross-traces
Although many funds are seated in an empty walk, increasing stakes to slide through the harder routes for cross chains. The report shows that 42.23% of stolen funds were moved to chains, bypassing the chain-specific monitoring system.
Fisun explained that bridges in transverse chains “had already become one of the best money laundering tools” to punch the chain-specific monitoring. And while repeated abuse could draw AML supervision, the Tornado Cash The case proves one thing: “The tactics of the eyeshadow, and do not require,” Fisun added.
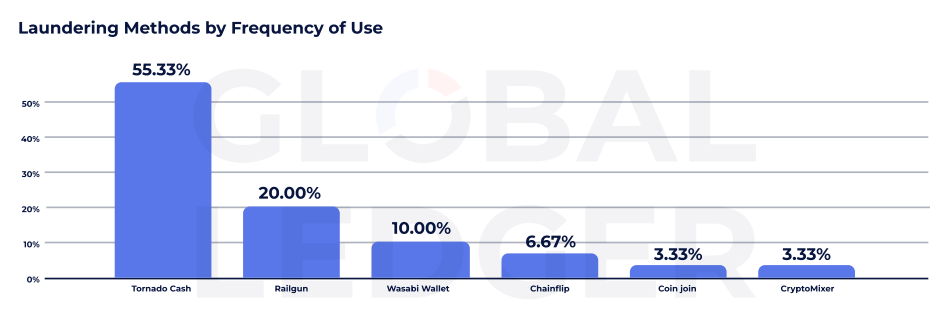
The data of the global book also shows that Tornado Money remains the dominant washing protocol, which is used in more than 50% of the cases that the firm follows. Despite the US Cashier sanctions In 2022. years and mounting the pressure of the controller in the global side, the service still plays a central role in post-hack laundry.
Its use is spread again after the verdict of the US court overturned sanctions on constitutional basis 2024. years.
Other privacy tools also get swing. Railway railway, for example, was used in 20% of cases, while Vasabi wallet appeared in 10%. Chainflip, coingjiin and criptomiker was involved in less than 7% of washing flows, data is displayed.
The attackers become smarter
Fisun noticed that slower flows through centralized exchange – now on average more than 425 hours – do not only reflect the better respect.
Both, said the global director of the book “is not a failure, it is a design” as attackers to encourage the Privacy to cross the stolen funds through the CEXs that “try to put down the streams that look shady.”
Only a small part of the funds is frozen with teams of execution or compliance. The report suggests that answers in real time remain rare, even as tools for analytics and supervision monitoring.
While the numbers indicate continuous challenges, they also underline where counsel can get the edge. Timelines – sometimes measured in days – show that there is still space to act before stolen funds disappear completely.
https://crypto.news/app/uploads/2023/12/crypto-news-biggest-crypto-hacks-option01.webp
2025-05-12 19:18:00