Guttong attacks Abuse hundreds of GitHub Repos to steal crypto


Malicial software campaign is used for gravity of hundreds of github repository to receive users to take information on information about information about the trojans (rats) and clipboard tribunals to steal crypts and credentials.
According to Kasperski, the Guttong is active for at least two years, targeting users on the global side, but with an elevated focus on Russia, Brazil and Turkey.
“During the Gitty campaign, the threats behind it created hundreds of fake malware projects – for example, an automation instrument to interact with Instagram accounts, telegram bot allowing you to manage the wallets in Bitcoin, and tools for hacking for video game valorant, ” describes Kasperski’s Georgi Kucherin.
Source: Kasperski
The researcher explains that false repository are made with care, given the details and the readmas written in the appropriate way, probably with the help of AI tools.
Moreover, actors threats hire tricks to artificially inflate the number of obligations submitted to these warehouses, creating a false image of high activity and increasing credibility.
Source: Kasperski
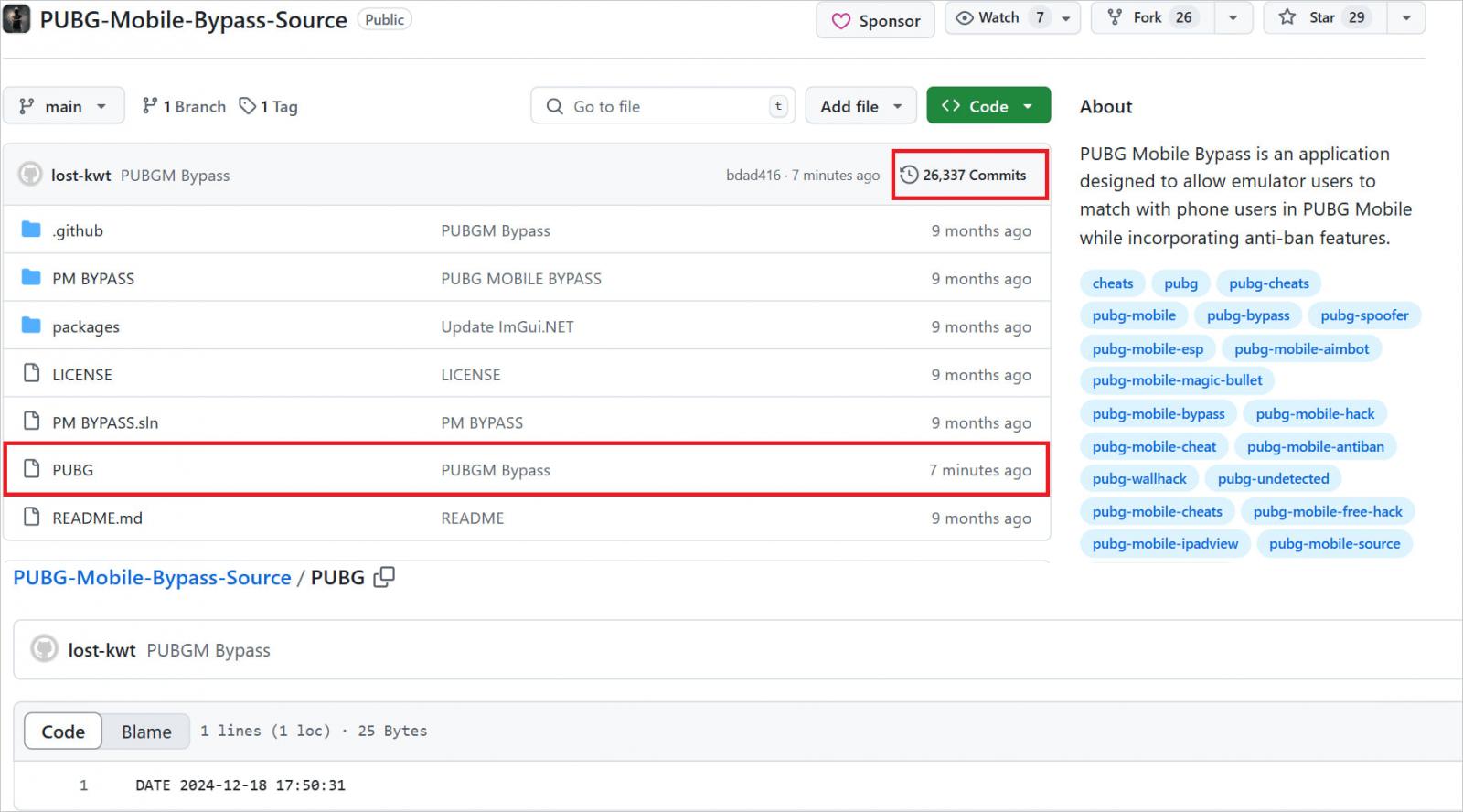
Malware in Github projects
Kasperski’s multiple warehouse analysis that supports the Guttal warehouse revealed that the malicious in injected in projects was written in various languages, including Python, JavaScript, C, C ++ and C #.
Different languages are considered to be used to avoid detection to specific tools or methods of codes preview.
Once the victim executes a useful load, injected at the assumes the second phase from the Github controlled attacker.
Kasperski found the following tools used in Gice:
- Node.js stealer – Infostealer which targets preserved credentials, information about the cryptocurrency wallet and browsing history. Compresses data in the archive of a .7z and throws it out through the telegram.
- Asyncrate – Open rats that allows remote control, keilogging, screen recording, file manipulation and command execution.
- Kuasar Backdoor – Open rat with opportunities similar to asyncrat companies.
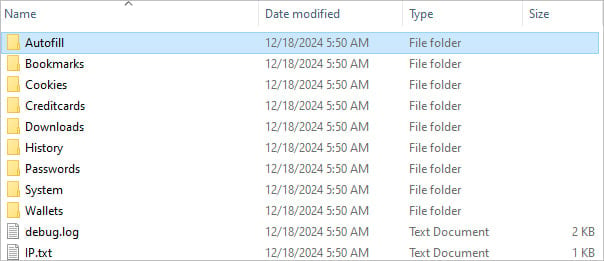
- Clipboard HIJACKER – malicious software that accompanies the victim’s clipboard for cryptocurrency wallet and replaces everything with the address under the attacker’s control, redirecting hacker.
The report expires one case from November 2024. when Bitcoin wallet attackers received 5 BTC, it is valued at half a million USD.
Source: Kasperski
Stay safe from this campaign
Although malicious software Hiding in GitHub with replays Under the wide of regular software or even Poc Exploits It is not new, gitnen’s duration and size prove that legitimate abuse of the platform continues to be very effective.
The key is to thoroughly veterinary project before use of any of its files inspection inspection, scan files with antivirus tools and execute downloaded files in an isolated environment.
The red flags include an overwhelming code, unusual automated liabilities and excessively detailed readme files that look ai-generated.
https://www.bleepstatic.com/content/hl-images/2025/02/25/GitHub.jpg
2025-02-25 22:45:00




